by Incrust Software
Share
What is the Bet Stop and How does Bet Stop – the National Self-Exclusion Register™ work?
Bet Stop – the National Self-Exclusion Register™ is a safe and free Australian Government initiative to block yourself from all licensed Australian online and phone gambling providers in a single process.
You can register at any time and you may self-exclude for a period you choose, from a minimum of three months up to a lifetime.
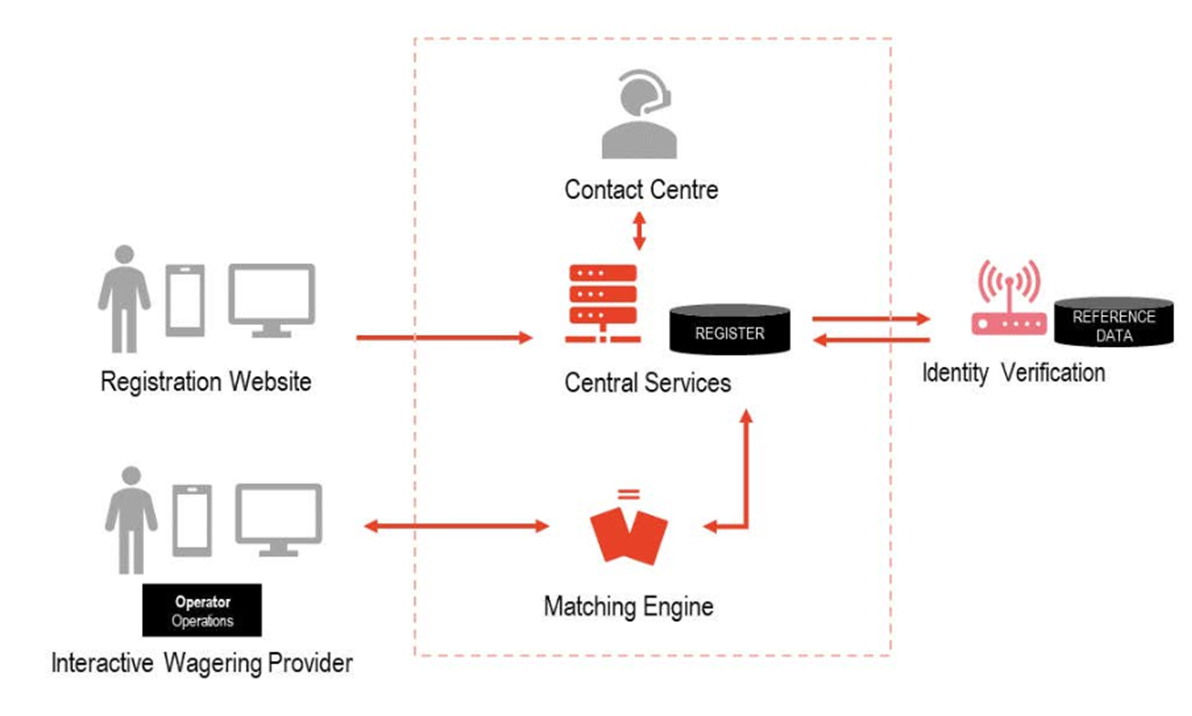
An account is created for users when they register and they are added to the register to self-excluded individuals. To ensure the accuracy of data in the matching service, each registered individual must have their identity verified before they are added to the register.
The matching service allows wagering providers to query the register to determine whether their customers are self-excluded.
Wagering providers can query the register through the API. Wagering providers need to log into their account to obtain an API key and whitelist their IP address/es to query the register.
What is the Bet Stop and How does Bet Stop – the National Self-Exclusion Register™ work?
What needs to be done in order for Bet Stop compliant?
Once customer register, online and phone gambling providers will not be able to:
- let you place a bet.
- let you open new betting accounts.
- send you marketing messages.
Providers should also close any accounts you have and refund any credit to you.
Gambling providers needs to integrate the Bet Stop matching service at the time of creating new account, user login, and when accepting a user bet to determine whether their customers are self-excluded and Also Need to remove excluded members from the marketing list.
What happens at the end of exclusion?
We will let you, and any support persons you have nominated, know before your exclusion period ends and ask you if you want to extend.
Once your exclusion period has ended, They will remove you from Bet Stop – the National Self-Exclusion Register. You will be able to self-exclude again at any time.
Bet Stop API call (Matching Service)
Test/Lab Environment :
Before connecting to the production environment, you should make use of the lab environment to test your integration. Individual and batch checks in the lab environment are not counted for cost recovery levy calculations.
The lab environment contains a set of test data with details for 32 test self-excluders. See “Matching Data in Lab” section below.
Lab configuration portal: https://iwp.lab.nser.cc/
Lab endpoint: https://chk.lab.nser.cc/
Production Environment :
Production configuration portal: https://iwp.betstop.gov.au/
Production endpoint: https://chk.betstop.gov.au/
All production check requests are logged for auditing purposes. Check requests in the production environment are subject to cost recovery levy calculations from the NSER proclamation date (21st of August, 2023).
Request:
{
“wagerer_id”:”BB2″,
“first_name”:”Jane”,
“last_name”:”Doe”,
“date_of_birth”:”1970-11-23″,
“email_address”:”[email protected]”,
“phone_number”:”0499999999″,
“postcode”:”0200″
}
Response:
HTTP/2 200
date: Mon, 11 Sep 2023 12:27:53 GMT
content-type: application/json
server: nginx
vary: Origin
vary: Access-Control-Request-Method
vary: Access-Control-Request-Headers
x-nser-request-id: b980c9c2-d500-49d3-b960-8e14d6bfafec
{“wagerer_id”:”BB2″,”match_found”:true}
TLS/SSL Requirement
The matching service API endpoints can only be accessed via HTTPS. The supported TLS cipher suites are:
TLS 1.3
TLS-AES-128-GCM-SHA256
TLS-AES-256-GCM-SHA384
TLS-CHACHA20-POLY1305-SHA256
TLS 1.2
ECDHE-ECDSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-GCM-SHA256
ECDHE-ECDSA-AES256-GCM-SHA384
ECDHE-RSA-AES256-GCM-SHA384
STAY IN THE LOOP
Subscribe to our free newsletter.
Websites are always prone to security risks. This may impact businesses. Strengthen your web portal’s security. Read through our article for some problems and actionable solutions to ensure your web portal is secured OpenSSL 1.1 is considered outdated and vulnerable Issue a new SSL certificate (CA) and update it in your apache SSL configuration file. […]